Implement Metric Filter to profile memory usage for AWS Lambda Functions in AWS CloudFormation
Not long ago I came across the problem that I wanted to know in detail how much of the allocated memory my individual lambda functions consumes.
Since memory consumption is not part of the standard Lambda metrics, I had to find an individual solution.
As each lambda execution logs the memory usage I thought about implementing a metric filter extracting this information to create a custom metric in AWS CloudWatch.
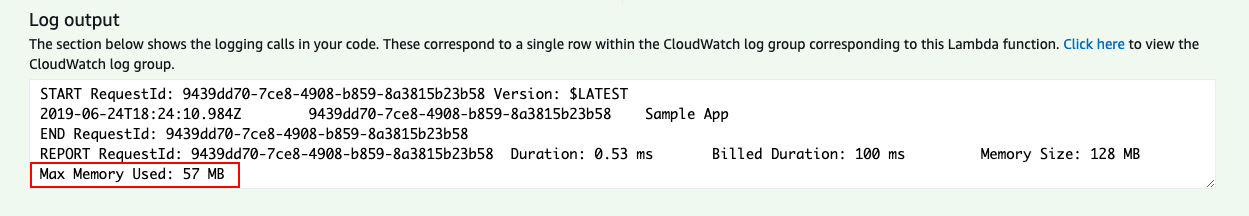
A sample metric filter was quickly found on the AWS forums (related thread).
You can test the metric filter by applying it to the log group of a lambda function like I did in the example below:
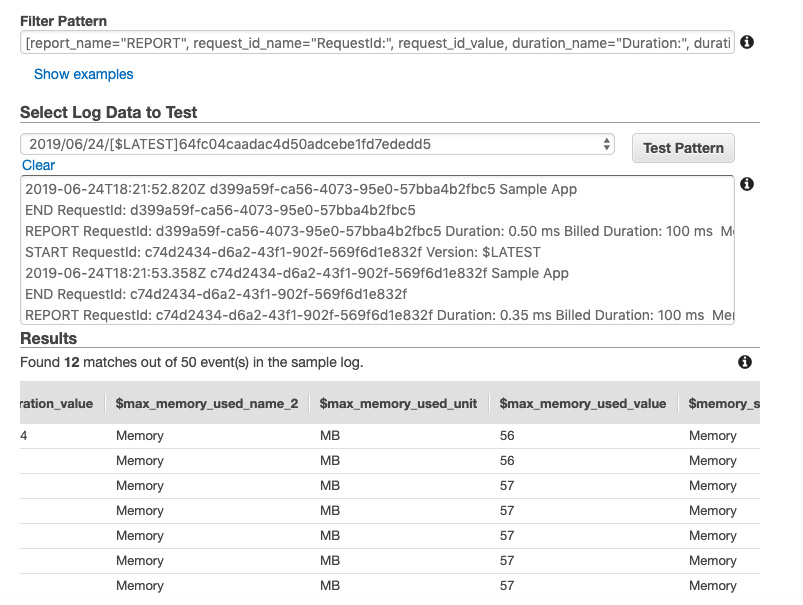
Now since verified the metric filter is actually working I only had to implement it in CloudFormation to be able to evaluate the memory consumption. It is important that a function name is defined so that the log group belonging to the Lambda function can also be created using the CloudFormation template.
You can find the template below:
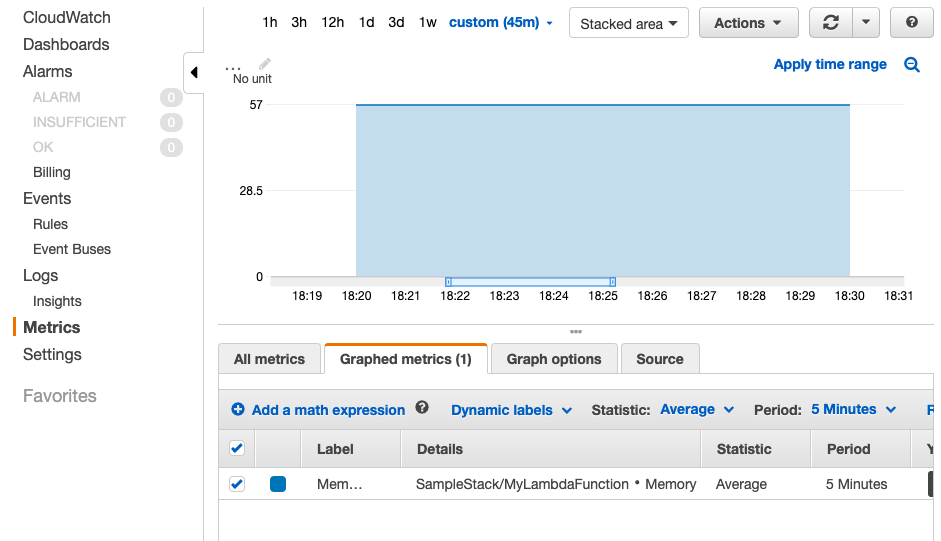
Now you can find the memory consumption metric under StackName > LambdaFunctionName > Memory in AWS CloudWatch:
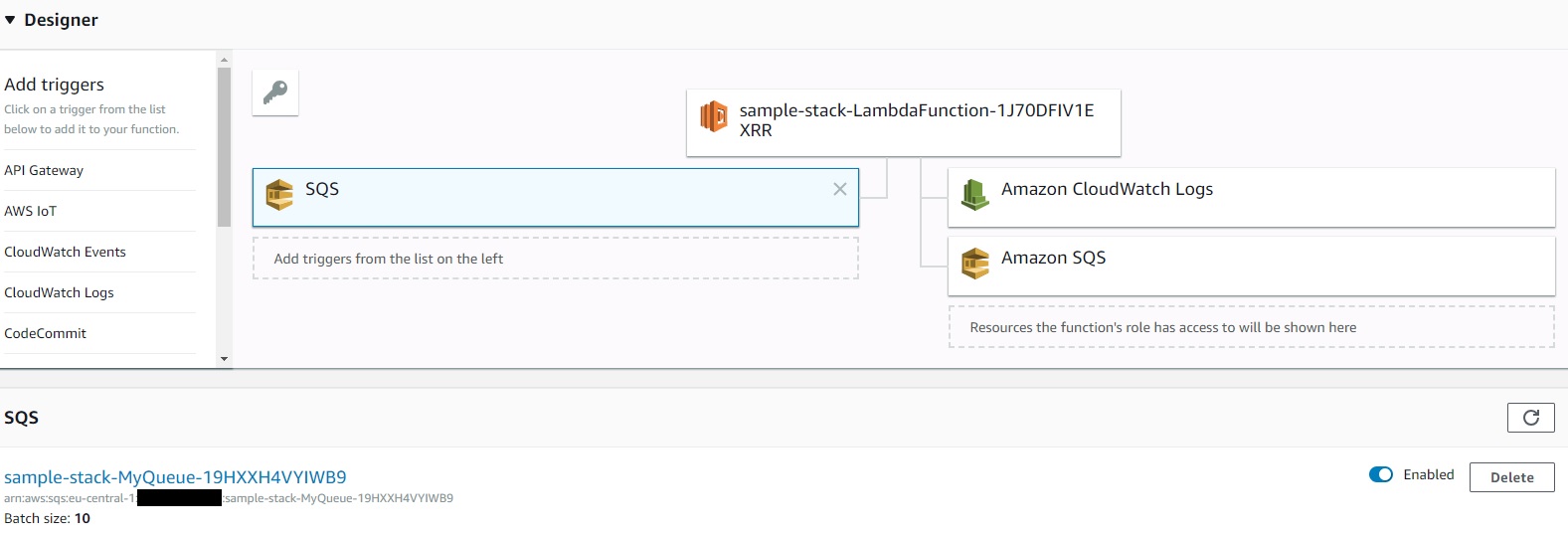
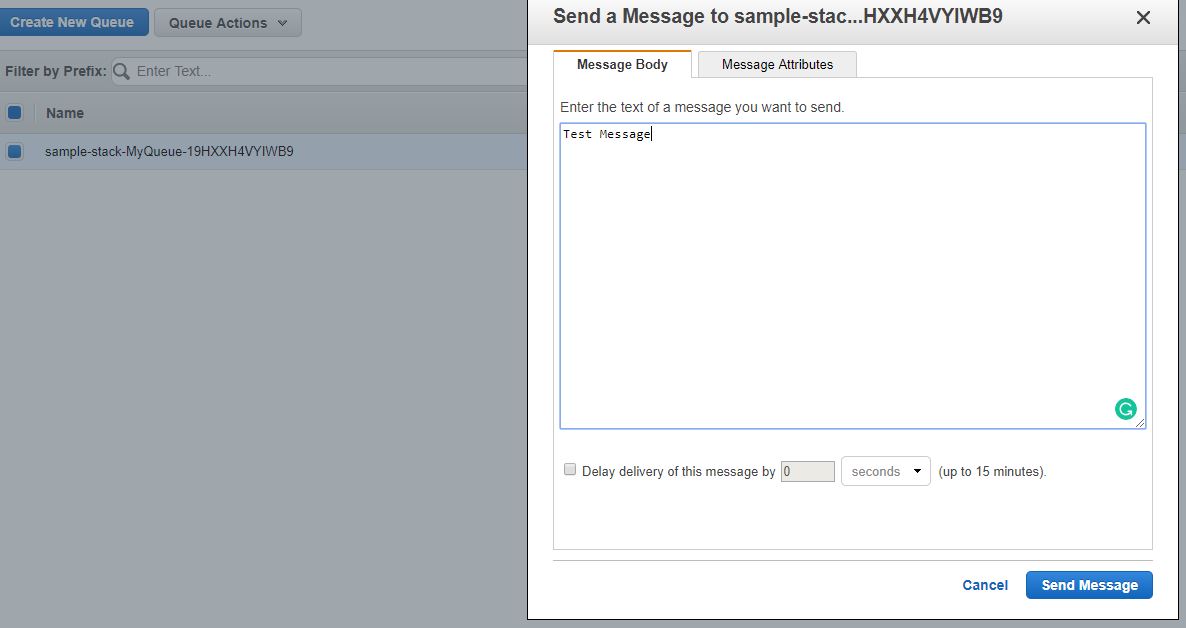 Sending a test message via the SQS Console
Sending a test message via the SQS Console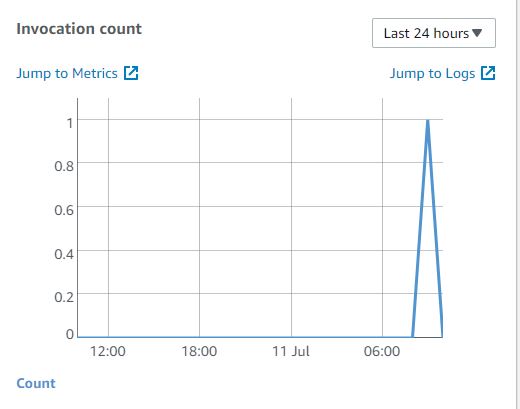 Check if the Lambda Function has been invoked
Check if the Lambda Function has been invoked
 AWS CodeBuild GitHub
AWS CodeBuild GitHub Sometimes its necessary to generate random passwords inside a CloudFormation template for instance to secure internet facing applications running on an EC2 or ECS instance. To achieve this you have the possibility to let the user of your Cloud Formation template insert passwords as parameters during the stack creation.
Sometimes its necessary to generate random passwords inside a CloudFormation template for instance to secure internet facing applications running on an EC2 or ECS instance. To achieve this you have the possibility to let the user of your Cloud Formation template insert passwords as parameters during the stack creation.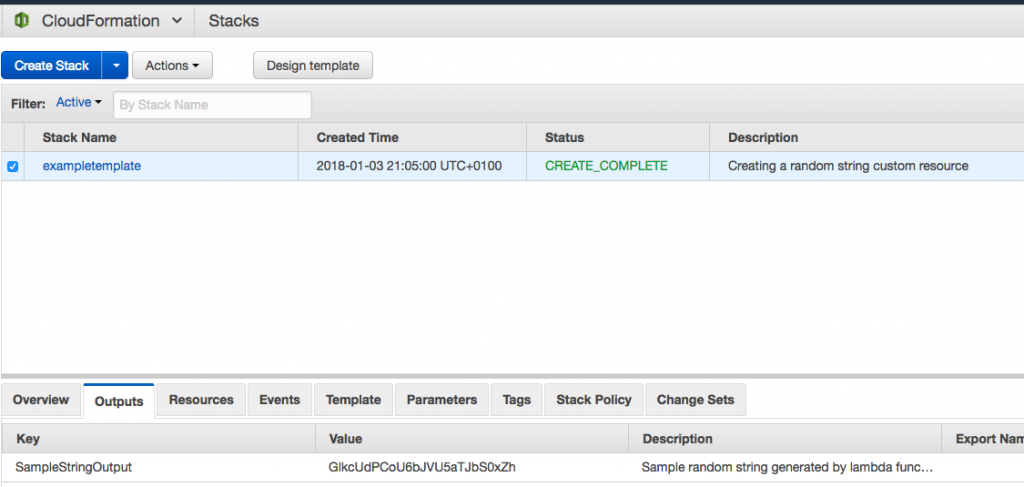 AWS Console CloudFormation
AWS Console CloudFormation